
- Importance of Container Security
- Security Challenges in Container Environments
- Top Container Security Tools
- Evaluation and Comparison
- Additional Best Practices for Container Security
- Conclusion
Importance of Container Security
In today’s fast-paced DevOps environments, the importance of container security cannot be overstated. Containers, especially platforms like Docker, offer unmatched flexibility and efficiency for deploying applications, but they also introduce new layers of risk if not properly secured. Docker container security focuses on protecting containerized applications from threats across the entire lifecycle from build to deployment and runtime by integrating best practices and Cyber Security Training to ensure teams are well-equipped to identify and mitigate vulnerabilities effectively. Since containers share the same OS kernel, a vulnerability in one container can jeopardize the entire host system. This makes it crucial to implement robust container security tools that continuously monitor for misconfigurations, vulnerabilities, and unauthorized access. Many organizations leverage open source container scanning solutions to detect known vulnerabilities in container images before they ever reach production. These tools not only help in identifying risks early but also integrate well with CI/CD pipelines for automated security enforcement. As cyber threats grow increasingly sophisticated, relying on manual checks or outdated security practices can lead to severe consequences, including data breaches and compliance violations. Investing in container security isn’t optional it’s essential for maintaining trust, uptime, and system integrity in modern cloud-native infrastructures. Whether you’re managing microservices or large-scale Kubernetes deployments, strong container security practices are your first line of defense.
Interested in Obtaining Your Cybercrime Certificate? View The Cyber Security Online Training Offered By ACTE Right Now!
Security Challenges in Container Environments
- Insecure Container Images: Many container images are pulled from public repositories, which may contain vulnerabilities. Without proper open source container scanning, these risks can slip into production unnoticed.
- Lack of Visibility and Monitoring: Containers are dynamic and short-lived, making it hard to track activity and detect threats. Traditional monitoring tools often fall short, highlighting the need for specialized container security tools and a foundational understanding of What Is The TCP/IP Model, as network-layer visibility is crucial for detecting suspicious behaviors in containerized environments.
- Misconfigurations: Incorrect configurations in containers, orchestrators (like Kubernetes), or Docker files can expose systems to attacks. Automating checks with security tools helps mitigate this risk.
Securing containerized environments has become a growing concern as organizations rapidly adopt container technology for scalability and efficiency. While tools like Docker simplify application deployment, they also bring unique security risks. Addressing these risks requires a deep understanding of the challenges and the right use of container security tools, including open source container scanning solutions and best practices for Docker container security.
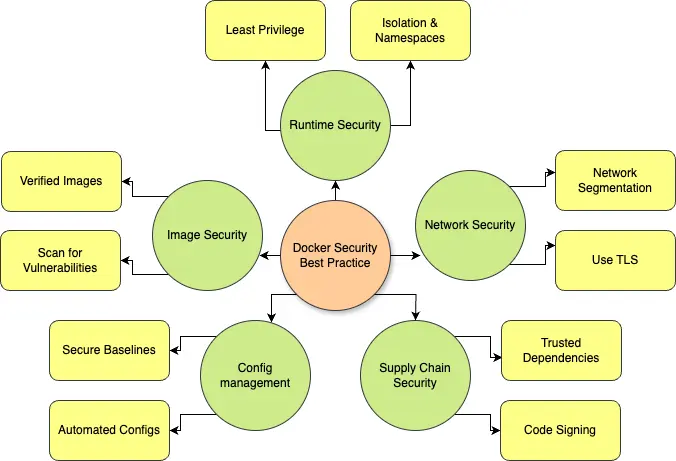
- Weak Isolation: Containers share the host OS kernel, and a single compromised container can affect others if isolation isn’t strong. Docker container security practices should enforce strict resource and process controls.
- Unsecured Secrets Management: Storing sensitive information like API keys or passwords within container images or environment variables poses a major risk.
- Inadequate Runtime Protection: Detecting anomalies during container runtime is essential. Without real-time protection, attacks can go unnoticed, especially in large-scale environments.
Top Container Security Tools
As container adoption accelerates, ensuring robust protection through the top container security tools has become essential for maintaining safe cloud-native environments. Containers like those managed via Docker streamline deployment but also introduce new security concerns, such as Docker security issues related to image vulnerabilities, misconfigurations, and inadequate access controls. Tools like Twistlock Kubernetes (now part of Palo Alto’s Prisma Cloud) provide comprehensive protection by integrating with orchestrators and continuously scanning for risks. A reliable container scanner plays a crucial role in identifying threats early, especially during the image build phase. These scanners help maintain Docker image security by detecting outdated packages, known CVEs, and policy violations before images are deployed. Effective Docker security also requires runtime monitoring, role-based access control, and network segmentation, all of which are offered by advanced container security platforms like Aqua Security, Sysdig Secure, and Anchore. It’s also essential to Explain What Is Bot in this context, as automated bots can exploit container vulnerabilities if not properly defended against through robust security measures. These tools not only scan for vulnerabilities but also enforce compliance rules and provide visibility into container activity. Given the growing sophistication of attacks targeting containerized environments, relying solely on traditional security solutions is no longer enough. A layered, automated, and continuous security strategy using top-rated tools is the best defense against evolving threats in the container ecosystem.
To Explore Cybersecurity in Depth, Check Out Our Comprehensive Cyber Security Online Training To Gain Insights From Our Experts!
Evaluation and Comparison
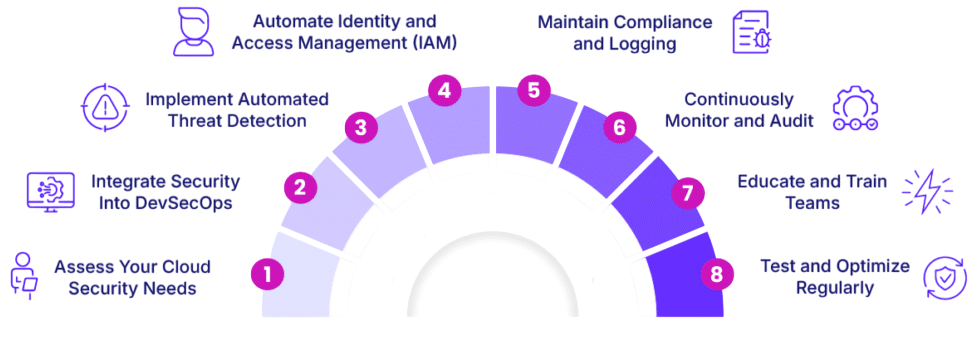
- Vulnerability Scanning Capabilities: Tools should offer deep open source container scanning to identify known CVEs in container images, with continuous updates for threat intelligence.
- Integration with CI/CD Pipelines: Effective Container Security Tools should seamlessly integrate with DevOps workflows to automate security at every stage of the container lifecycle, while also incorporating Cyber Security Training to equip teams with the knowledge to identify and respond to threats proactively.
- Runtime Threat Detection: Look for tools that go beyond static analysis and provide real-time monitoring for anomalies, ensuring stronger Docker container security during execution.
When selecting the right security solutions for containerized environments, a clear evaluation and comparison of available options is essential. With a wide array of Container Security Tools on the market, organizations must assess them based on their capabilities, compatibility, and ease of integration. Whether you’re focusing on Docker container security or enterprise-scale orchestration like Kubernetes, each tool offers unique strengths. Here’s a breakdown of key evaluation criteria:
Additional Best Practices for Container Security
Beyond using the right tools, implementing additional best practices for container security is crucial for maintaining a secure and resilient containerized environment. As Docker security becomes more critical in modern DevOps workflows, teams must go beyond basic setups to address evolving threats. Regularly scanning images with a trusted container scanner ensures vulnerabilities are identified early in the build process. To reduce Docker security issues, always use minimal and verified base images, avoid running containers as root, and apply the principle of least privilege. Continuous monitoring tools like Twistlock Kubernetes enhance visibility and automate threat detection across orchestrated environments, helping prevent attacks before they escalate. Integrating encryption methods such as the Data Encryption Standard Algorithm further strengthens data protection within containerized systems, ensuring sensitive information remains secure. Additionally, ensuring Docker image security involves signing images, enabling content trust, and performing regular image updates. Secure network configurations and segmentation between containers further reduce attack surfaces. Managing secrets properly by using secure vaults instead of hardcoding them into containers is another vital practice. It’s also important to audit container activity logs regularly and restrict user access based on roles. Together, these best practices create a multi-layered defense strategy that strengthens container ecosystems against internal misconfigurations and external threats, ensuring secure application delivery and operational integrity across all environments.
Preparing for Cyber Security Job Interviews? Have a Look at Our Blog on Cyber Security Interview Questions and Answers To Ace Your Interview!
Conclusion
In conclusion, securing containerized environments is no longer optional it’s a necessity in today’s fast-moving, cloud-native development landscape. With the rapid adoption of container technologies, implementing robust Container Security Tools is essential to safeguard applications throughout their lifecycle. From image creation to deployment and runtime, every stage must be protected using reliable solutions that offer vulnerability scanning, compliance enforcement, and real-time threat detection. Docker container security plays a pivotal role, especially since Docker remains one of the most widely used container platforms. Addressing Docker-specific risks like image vulnerabilities, misconfigurations, and unauthorized access requires dedicated strategies, tools, and comprehensive Cyber Security Training to ensure teams can effectively secure their container environments. Leveraging open source container scanning tools adds an extra layer of protection by identifying known CVEs and misconfigurations early, without the need for costly proprietary solutions. These scanners can be easily integrated into CI/CD pipelines, ensuring security is embedded from the start. As containerized environments grow more complex, a proactive, layered, and automated approach is the key to maintaining operational resilience. Whether you’re securing a small Docker-based application or a large Kubernetes cluster, combining best practices with the right security tools ensures a strong defense against evolving threats. Ultimately, investing in comprehensive container security safeguards your infrastructure, data, and business continuity.



